How Are Session Keys Generated
Microsoft Office 365 Product Key Generator used for activation of Microsoft Office product full version free. Microsoft Office is the complete product that developed by Microsoft corporation. Microsoft Office 365 Product Key is a complete all-in-one package of tools that support to make office full version to use its all features easily and freely. Office 2016 product key crack. Jan 14, 2020 Microsoft Office 365 Key Features: Microsoft Office 36 Product Key Turbine may be work statically and regularly anywhere without disruption, with the capacity to function separately of the unit and help similar interfaces on each device. All plans are appropriate for Office 2007, Office 2008 for Mac, Office 2010, and Office 2011 for Mac.
- How Are Session Keys Generated 2017
- Session Keys Electric S
- How Are Session Keys Generated Made
- How Are Session Keys Generated 2018
- How Are Session Keys Generated Energy
- RandomKeygen is a free mobile-friendly tool that offers randomly generated keys and passwords you can use to secure any application, service or device. KEY RandomKeygen - The.
- What you want to do is to flat-out remove expired sessions, or at least the non-permanent ones. If you cannot do this, add a field to your table and name it sessionexpired, set it to boolean. Instead of indexing with sessionid, index with sessionid,sessionexpired. This gives you twice the scope, but will not reduce database seek time.
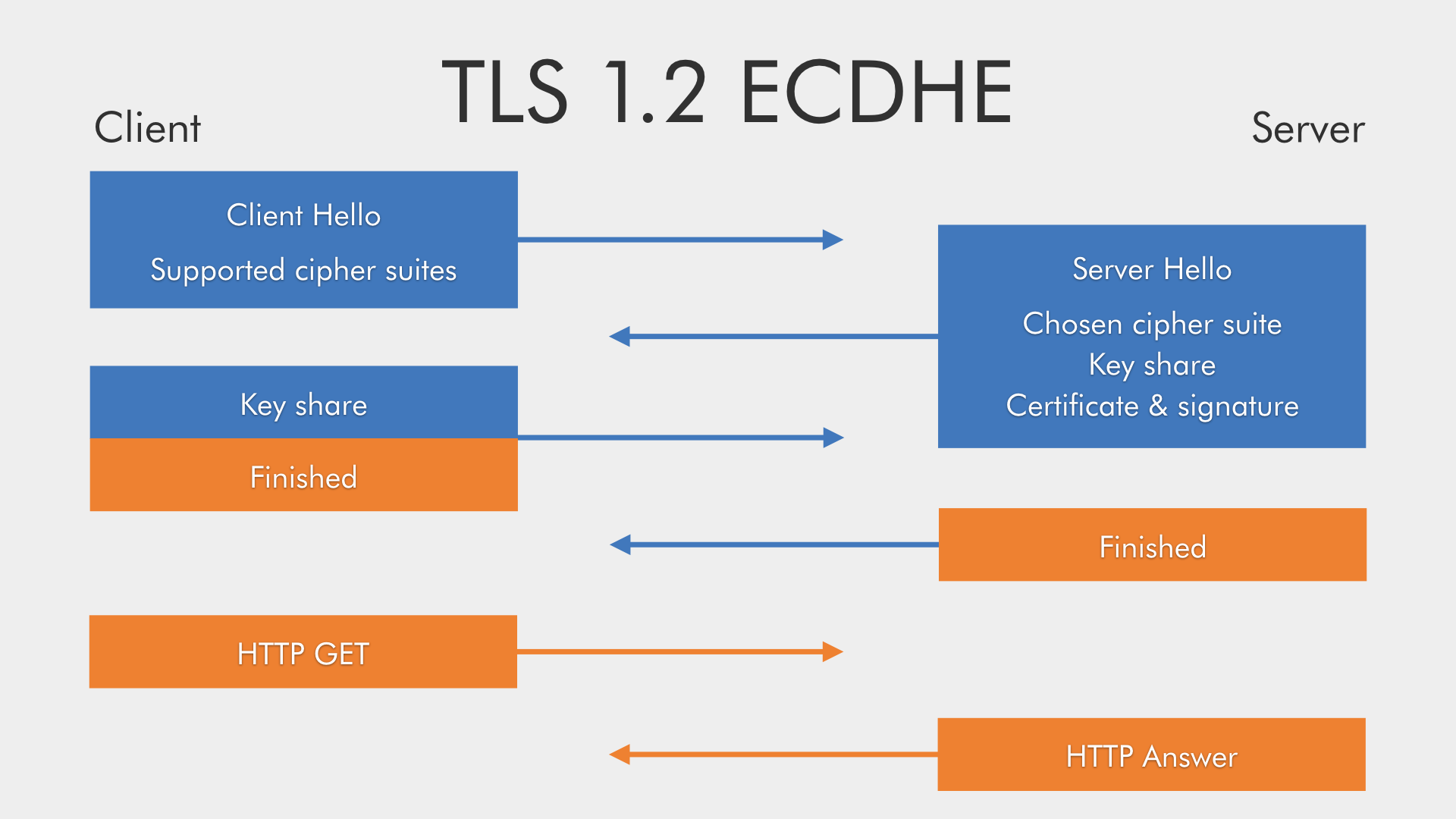
- Now, this key can be either used as an encryption key or a MAC key. It simply has to be a symmetric and valid for a particular session. In context of TLS, people usually use the term session keys for the four keys derived from the Master Secret (client write MAC key, server write MAC key, client write encryption key, and server write encryption.
Session keys are keys that are generated to be used in a single communication session. Session keys are frequently changed and are discarded when they are no longer needed. For example, TLS uses a separate session key for each connection and S/MIME uses a separate session key for each email message. Typically a symmetric key is used as the session key.
The browser in return makes a pseudo-randomly generated symmetric from mouse clicks a key presses and encrypts the public key with it. On the other side, the site upon receiving the encrypted public key, uses its private key to decrypt it. Create Session Key Example.; 2 minutes to read; In this article. The session key is used to protect the content key. The following code demonstrates how to create a session key, but leaves out the details of random key generation. What Happens in a TLS Handshake? SSL Handshake. In a TLS/SSL handshake, clients and servers exchange SSL certificates, cipher suite requirements, and randomly generated data for creating session keys.
Session keys are volatile. Applications can save these keys for later use or for transmission to other users. For more information, see Cryptographic Key Storage and Exchange.
How to start a remote session using Bomgar Representative Console.
How Are Session Keys Generated 2017
Login to Bomgar Representative Console and select the Session Key radio button. This will generate a one-time key for the client to input on their end. From the Session Key window, you will be able to set an expiration time on the key, if the client is not currently at their computer.
IObit Driver Booster Full Key Crack With Serial Key (Windows / Mac)IObit Driver Booster Pro Keygen appreciates and recognized the customer requires and presents its amazing structure 6.0.2 iObit pro split with the sequential break. Driver booster full, Various reviving programming which is used to this propelled world not invigorated programming driver immediately which presented on the working structure and lifts the system speed. Various patrons have a generous weight which takes so much time to download and invigorate drivers and programming.  Along these lines, reason bit 5 design in a lightweight and it can manage the driver immediately.
Along these lines, reason bit 5 design in a lightweight and it can manage the driver immediately.
Have client visit: https://remote.uillinois.edu. The website will prompt client to enter session key:
Once the client enters the session key and presses submit, the following will appear:

Session Keys Electric S
Have client follow onscreen prompts. A window should appear briefly, showing client that their computer is connecting to the server. Followed by and end user agreement which they will need to agree to:
When client has agreed to the terms, they will pop up in your Bomgar session window:
Double clicking the client session will open up a new window, you will need to click Screen Sharing to prompt the client to allow or refuse remote access:
How Are Session Keys Generated Made
Once the user allows remote access, you will be able to see their desktop; which includes multiple monitors. You will now have access to all parts of the computer, unless admin rights are needed. (If the user has admin rights, it will prompt them to select allow, while a loading symbol will appear on your end.) Pressing the red X in the right corner of the screen, will allow you to end the session. Session Info will give more detailed information of the client’s computer.
How Are Session Keys Generated 2018
See Also:
How Are Session Keys Generated Energy
| Keywords: | Bomgar, remote, remote session, chat session, remote login, AITSSuggest keywords | Doc ID: | 55015 |
|---|---|---|---|
| Owner: | JC S. | Group: | University of Illinois System |
| Created: | 2015-08-12 20:01 CDT | Updated: | 2018-05-16 14:57 CDT |
| Sites: | University of Illinois at Chicago ACCC, University of Illinois at Springfield, University of Illinois System, University of Illinois Technology Services | ||
| Feedback: | 40CommentSuggest a new documentSubscribe to changes | ||