Key Generation In Elliptic Curve Cryptography
- Key Generation In Elliptic Curve Cryptography Algorithm With Example
- Key Generation In Elliptic Curve Cryptography Free
Oct 04, 2018 Elliptic curve cryptography, or ECC, is a powerful approach to cryptography and an alternative method from the well known RSA. It is an approach used for public key encryption by utilizing the mathematics behind elliptic curves in order to generate security between key pairs. Oct 04, 2018 Elliptic Curve Cryptography, or ECC, is a powerful approach to cryptography and an alternative method from the well known RSA. It is an approach used for public key encryption by utilizing the mathematics behind elliptic curves in order to generate security between key pairs. Elliptical curve cryptography (ECC) is a public key encryption technique based on elliptic curve theory that can be used to create faster, smaller, and more efficient cryptographic keys.
Definition
Provides an abstract base class that encapsulates the Elliptic Curve Digital Signature Algorithm (ECDSA).
- Derived
Remarks
This class serves as the abstract base class for ECDsaCng derivations.
Aug 24, 2017 Running php artisan key:generate in a Laravel project where the.env file does not contain an APPKEY= line results in the following output: Application key base64:KEYHERE= set successfully. However, the key is not written to the.env file, so the status message is incorrect. Steps To Reproduce: Create a.env file without an APPKEY= line. Dec 07, 2016 php artisan key:generate Regenerating the Application Key It is important to note that if the encryption key needs to be regenerated after an application has been in use, any data that was previously encrypted using the old key cannot be decrypted using the new encryption key. Php artisan key generate reset.
Constructors
| ECDsa() | Initializes a new instance of the ECDsa class. |
Fields
| KeySizeValue | Represents the size, in bits, of the key modulus used by the asymmetric algorithm. (Inherited from AsymmetricAlgorithm) |
| LegalKeySizesValue | Specifies the key sizes that are supported by the asymmetric algorithm. (Inherited from AsymmetricAlgorithm) |
Properties
| KeyExchangeAlgorithm | Gets the name of the key exchange algorithm. |
| KeySize | Gets or sets the size, in bits, of the key modulus used by the asymmetric algorithm. (Inherited from AsymmetricAlgorithm) |
| LegalKeySizes | Gets the key sizes that are supported by the asymmetric algorithm. (Inherited from AsymmetricAlgorithm) |
| SignatureAlgorithm | Gets the name of the signature algorithm. |
Methods
| Clear() | Releases all resources used by the AsymmetricAlgorithm class. (Inherited from AsymmetricAlgorithm) |
| Create() | Creates a new instance of the default implementation of the Elliptic Curve Digital Signature Algorithm (ECDSA). |
| Create(ECCurve) | Creates a new instance of the default implementation of the Elliptic Curve Digital Signature Algorithm (ECDSA) with a newly generated key over the specified curve. |
| Create(ECParameters) | Creates a new instance of the default implementation of the Elliptic Curve Digital Signature Algorithm (ECDSA) using the specified parameters as the key. |
| Create(String) | Creates a new instance of the specified implementation of the Elliptic Curve Digital Signature Algorithm (ECDSA). |
| Dispose() | Releases all resources used by the current instance of the AsymmetricAlgorithm class. (Inherited from AsymmetricAlgorithm) |
| Dispose(Boolean) | Releases the unmanaged resources used by the AsymmetricAlgorithm class and optionally releases the managed resources. (Inherited from AsymmetricAlgorithm) |
| Equals(Object) | Determines whether the specified object is equal to the current object. (Inherited from Object) |
| ExportECPrivateKey() | Exports the current key in the ECPrivateKey format. |
| ExportEncryptedPkcs8PrivateKey(ReadOnlySpan<Byte>, PbeParameters) | Exports the current key in the PKCS#8 EncryptedPrivateKeyInfo format with a byte-based password. (Inherited from AsymmetricAlgorithm) |
| ExportEncryptedPkcs8PrivateKey(ReadOnlySpan<Char>, PbeParameters) | Exports the current key in the PKCS#8 EncryptedPrivateKeyInfo format with a char-based password. (Inherited from AsymmetricAlgorithm) |
| ExportExplicitParameters(Boolean) | When overridden in a derived class, exports the explicit parameters for an elliptic curve. |
| ExportParameters(Boolean) | When overridden in a derived class, exports the named or explicit parameters for an elliptic curve. If the curve has a name, the Curve field contains named curve parameters, otherwise it contains explicit parameters. |
| ExportPkcs8PrivateKey() | Exports the current key in the PKCS#8 PrivateKeyInfo format. (Inherited from AsymmetricAlgorithm) |
| ExportSubjectPublicKeyInfo() | Exports the public-key portion of the current key in the X.509 SubjectPublicKeyInfo format. (Inherited from AsymmetricAlgorithm) |
| FromXmlString(String) | This method throws in all cases. |
| GenerateKey(ECCurve) | When overridden in a derived class, generates a new ephemeral public/private key pair for the specified curve, replacing the current key. |
| GetHashCode() | Serves as the default hash function. (Inherited from Object) |
| GetType() | Gets the Type of the current instance. (Inherited from Object) |
| HashData(Byte[], Int32, Int32, HashAlgorithmName) | When overridden in a derived class, computes the hash value of the specified portion of a byte array by using the specified hashing algorithm. |
| HashData(Stream, HashAlgorithmName) | When overridden in a derived class, computes the hash value of the specified binary stream by using the specified hashing algorithm. |
| ImportECPrivateKey(ReadOnlySpan<Byte>, Int32) | Imports the public/private keypair from an ECPrivateKey structure, replacing the keys for this object. |
| ImportEncryptedPkcs8PrivateKey(ReadOnlySpan<Byte>, ReadOnlySpan<Byte>, Int32) | Imports the public/private keypair from a PKCS#8 EncryptedPrivateKeyInfo structure after decrypting with a byte-based password, replacing the keys for this object. |
| ImportEncryptedPkcs8PrivateKey(ReadOnlySpan<Char>, ReadOnlySpan<Byte>, Int32) | Imports the public/private keypair from a PKCS#8 EncryptedPrivateKeyInfo structure after decrypting with a char-based password, replacing the keys for this object. |
| ImportParameters(ECParameters) | When overridden in a derived class, imports the specified parameters. |
| ImportPkcs8PrivateKey(ReadOnlySpan<Byte>, Int32) | Imports the public/private keypair from a PKCS#8 PrivateKeyInfo structure after decryption, replacing the keys for this object. |
| ImportSubjectPublicKeyInfo(ReadOnlySpan<Byte>, Int32) | Imports the public key from an X.509 SubjectPublicKeyInfo structure after decryption, replacing the keys for this object. |
| MemberwiseClone() | Creates a shallow copy of the current Object. (Inherited from Object) |
| SignData(Byte[], HashAlgorithmName) | Computes the hash value of the specified byte array using the specified hash algorithm and signs the resulting hash value. |
| SignData(Byte[], Int32, Int32, HashAlgorithmName) | Computes the hash value of a portion of the specified byte array using the specified hash algorithm and signs the resulting hash value. License Keys for WooCommerce is a simple and powerfull license keys manager, that adds a new product type to your WordPress and WooCommerce setup, and lets you create and handle license keys that can be used to validate your licensed products. This plugin will enable your WordPress setup to act as a validator API (service). Generate license keys in wordpress free. Create license keys in your system (license server) Check the status of a license key from from your application (remotely) Activate a license key from your application (remotely) Deactivate a license key (remotely) Check a license key (remotely) Track where the license key is being used. About WordPress Secret Key Generator. This is a simple tool to generate WordPress Security Keys also known as WordPress Secret Keys for WordPress. |
| SignData(Stream, HashAlgorithmName) | Computes the hash value of the specified stream using the specified hash algorithm and signs the resulting hash value. |
| SignHash(Byte[]) | Generates a digital signature for the specified hash value. |
| ToString() | Returns a string that represents the current object. (Inherited from Object) |
| ToXmlString(Boolean) | This method throws in all cases. |
| TryExportECPrivateKey(Span<Byte>, Int32) | Attempts to export the current key in the ECPrivateKey format into a provided buffer. |
| TryExportEncryptedPkcs8PrivateKey(ReadOnlySpan<Byte>, PbeParameters, Span<Byte>, Int32) | Attempts to export the current key in the PKCS#8 EncryptedPrivateKeyInfo format into a provided buffer, using a byte-based password. |
| TryExportEncryptedPkcs8PrivateKey(ReadOnlySpan<Char>, PbeParameters, Span<Byte>, Int32) | Attempts to export the current key in the PKCS#8 EncryptedPrivateKeyInfo format into a provided buffer, using a char-based password. |
| TryExportPkcs8PrivateKey(Span<Byte>, Int32) | Attempts to export the current key in the PKCS#8 PrivateKeyInfo format into a provided buffer. |
| TryExportSubjectPublicKeyInfo(Span<Byte>, Int32) | Attempts to export the current key in the X.509 SubjectPublicKeyInfo format into a provided buffer. |
| TryHashData(ReadOnlySpan<Byte>, Span<Byte>, HashAlgorithmName, Int32) | Attempts to compute the hash value of the specified read-only span of bytes into the provided destination by using the specified hashing algorithm. |
| TrySignData(ReadOnlySpan<Byte>, Span<Byte>, HashAlgorithmName, Int32) | Attempts to compute the ECDSA digital signature for the specified read-only span of bytes into the provided destination by using the specified hashing algorithm and the current key. |
| TrySignHash(ReadOnlySpan<Byte>, Span<Byte>, Int32) | Attempts to compute the ECDSA digital signature for the specified read-only span of bytes representing a data hash into the provided destination by using the current key. |
| VerifyData(Byte[], Byte[], HashAlgorithmName) | Verifies that a digital signature is appropriate for the current key and provided data with a specified hash algorithm. |
| VerifyData(Byte[], Int32, Int32, Byte[], HashAlgorithmName) | Verifies that a digital signature is appropriate for the current key and provided portion of data with a specified hash algorithm. |
| VerifyData(ReadOnlySpan<Byte>, ReadOnlySpan<Byte>, HashAlgorithmName) | Verifies that a digital signature is appropriate for the current key and provided data with a specified hash algorithm. |
| VerifyData(Stream, Byte[], HashAlgorithmName) | Verifies that a digital signature is appropriate for the current key and provided data with a specified hash algorithm. |
| VerifyHash(Byte[], Byte[]) | Verifies that a digital signature is appropriate for the current key and provided data hash. |
| VerifyHash(ReadOnlySpan<Byte>, ReadOnlySpan<Byte>) | Verifies that a digital signature is appropriate for the current key and provided data hash. |
Explicit Interface Implementations
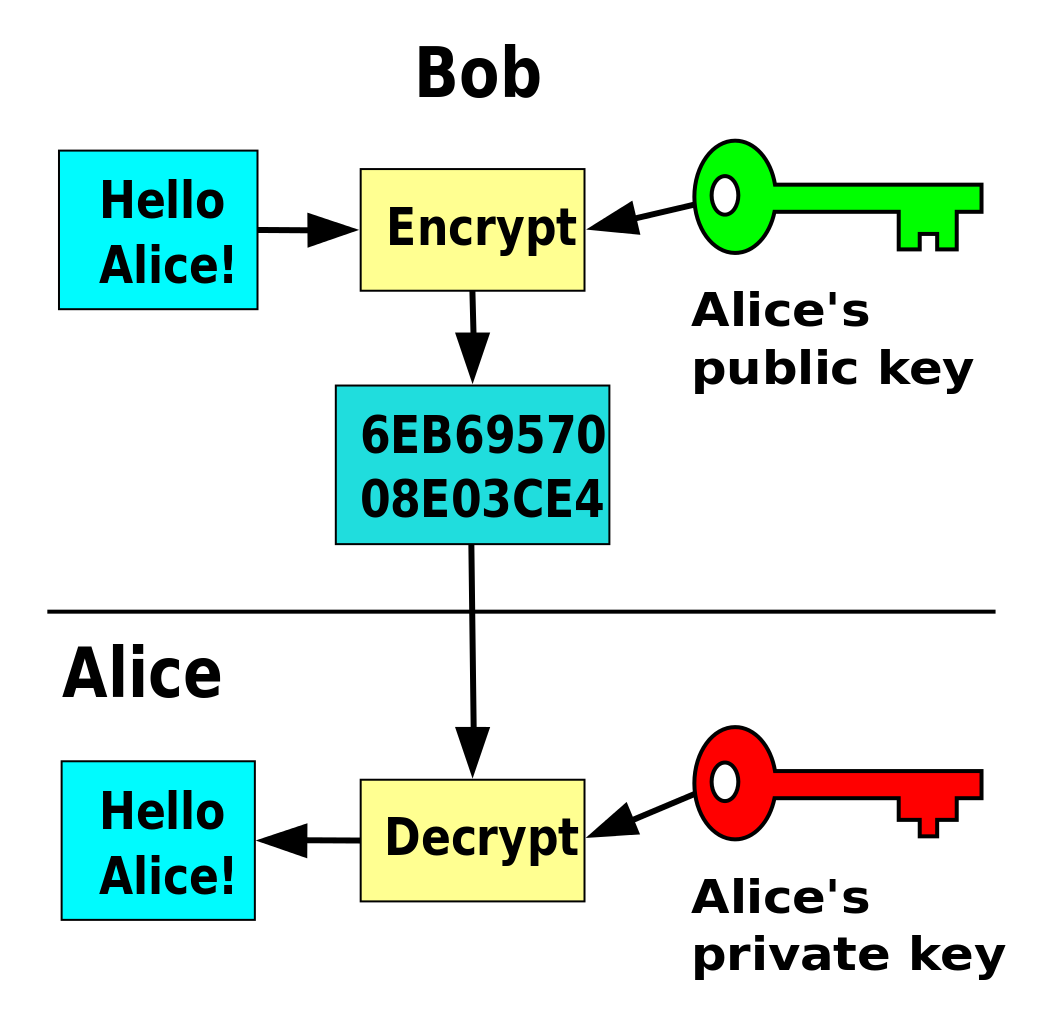
Key Generation In Elliptic Curve Cryptography Algorithm With Example
| IDisposable.Dispose() | For a description of this member, see Dispose(). (Inherited from AsymmetricAlgorithm) |