Openssl Generate Ecdh Key Pair
Online serial generator. Open full screen to view more.
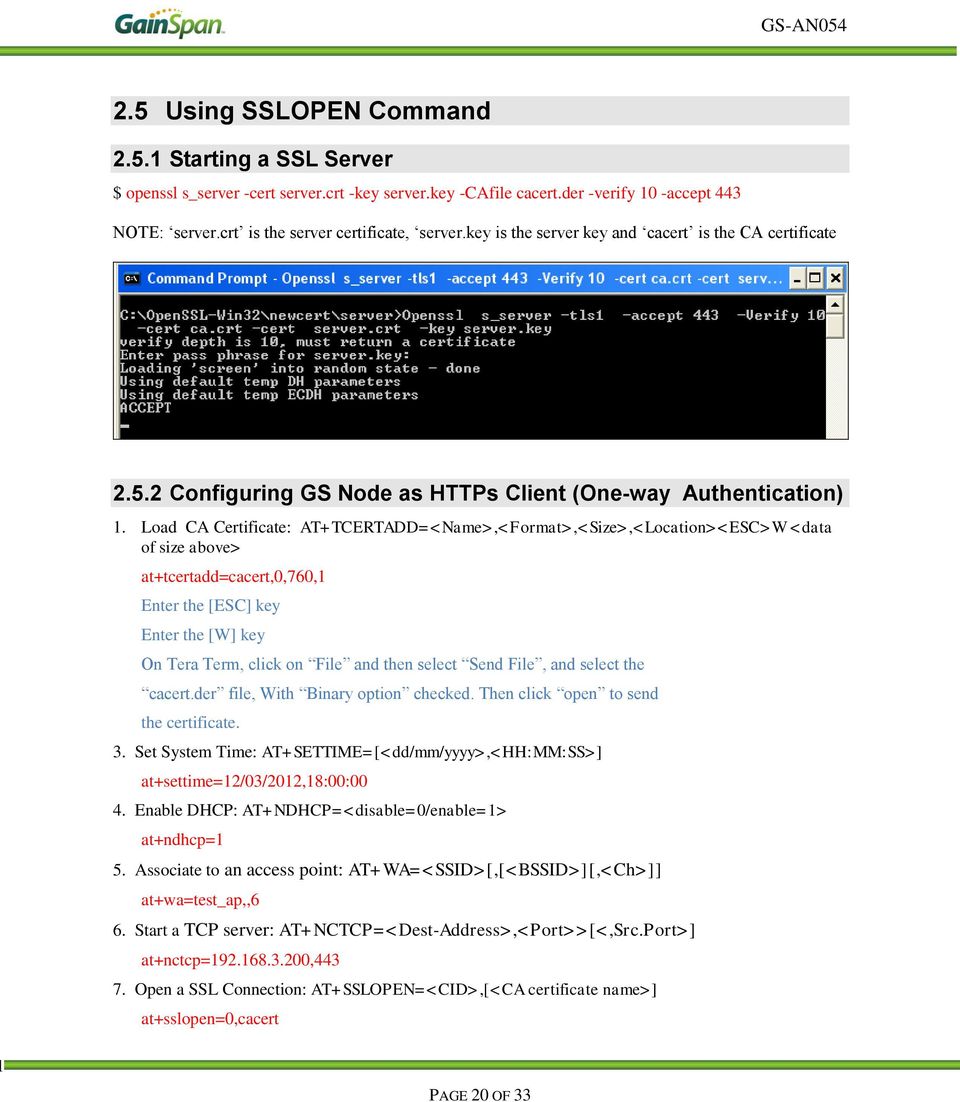
To perform the following actions for Windows or Linux, you must have OpenSSL installed on your system.
- Mar 03, 2020 Generating an Elliptic Curve keys You can use the following commands to generate a P-256 Elliptic Curve key pair: openssl ecparam -genkey -name prime256v1 -noout -out ecprivate.pem openssl ec.
- Learn in this article how to create elliptic curve (EC) keys for your public key infrastructure (PKI) and your certificate authority (CA). We will use the Elliptic Curve Diffie Hellman (ECDH) as keyagreement along with Elliptic Curve Digital Signature Algorithm (ECDSA) for signing/verifying.
- Jul 01, 2011 Creating server/client certificate pair using OpenSSL. The server/client certificate pair can be used when an application trying to access a web service which is configured to authenticate the client application using the client ssl certificates.
- Apr 17, 2017 Upon client receive this message it will send ClientVerifiy matched with ssl3sendclientkeyexchange. And in case of ECDH(E) openssl generate key pair using ECKEYgeneratekey (not engine's genkey) As you can see the patch: 'ecdhepatch.diff' you add ECDHgeneratekey function in server key exchange to accelerate computation.
- Apr 15, 2020 The ability to create, manage, and use public and private key pairs with KMS enables you to perform digital signing operations using RSA and Elliptic Curve (ECC) keys. You can also perform public key encryption or decryption operations using RSA keys. For example, you can use ECC or RSA private keys to generate digital signatures.
$ openssl rsa -pubout -in privatekey.pem -out publickey.pem writing RSA key A new file is created, publickey.pem, with the public key. It is relatively easy to do some cryptographic calculations to calculate the public key from the prime1 and prime2 values in the public key file. However, OpenSSL has already pre-calculated the public key.
Generating the Private Key -- Windows
In Windows:

1. Open the Command Prompt (Start > Programs > Accessories > Command Prompt).
2. Navigate to the following folder:
C:Program FilesListManagertclwebbincerts
3. Type the following:
openssl genrsa -out rsa.private 1024
4. Press ENTER. The private key is generated and saved in a file named 'rsa.private' located in the same folder.
NOTE The number '1024' in the above command indicates the size of the private key. You can choose one of five sizes: 512, 758, 1024, 1536 or 2048 (these numbers represent bits). The larger sizes offer greater security, but this is offset by a penalty in CPU performance. We recommend the best practice size of 1024.
Openssl Generate Ecdh Key Pair Free
Generating the Public Key -- Windows
1. At the command prompt, type the following:
openssl rsa -in rsa.private -out rsa.public -pubout -outform PEM
2. Press ENTER. The public key is saved in a file named rsa.public located in the same folder.
Generating the Private Key -- Linux
1. Open the Terminal.
2. Navigate to the folder with the ListManager directory.
3. Type the following:
openssl genrsa -out rsa.private 1024
4. Press ENTER. The private key is generated and saved in a file named 'rsa.private' located in the same folder.
Generating the Public Key -- Linux
1. Open the Terminal.
2. Type the following:
openssl rsa -in rsa.private -out rsa.public -pubout -outform PEM
2. Press ENTER. The public key is saved in a file named rsa.public located in the same folder.
How to generate keys in PEM formatusing the OpenSSL command line tools?
Openssl Generate Ecdh Key Pair Key
RSA keys
The JOSE standard recommends a minimum RSA key size of 2048 bits.
To generate a 2048-bit RSA private + public key pair for use in RSxxx and PSxxxsignatures:
Elliptic Curve keys
To generate an EC key pair the curve designation must be specified. Note thatJOSE ESxxx signatures require P-256, P-384 and P-521 curves (see theircorresponding OpenSSL identifiers below).
Elliptic Curve private + public key pair for use with ES256 signatures:
Elliptic Curve private + public key pair for use with ES384 signatures:
Elliptic Curve private + public key pair for use with ES512 signatures:
PEM key parsing in Java
The BouncyCastle library provides a simpleutility to parse PEM-encoded keys in Java, to use them for JWS or JWE later.
For Maven you should include the following BouncyCastle dependencies (where1.52 is the latest stable version as of May 2015):
Openssl Create Crt And Key
Example parsing of an PEM-encoded EC key in Java: