What Keys Are Generated During The Bluetooth Pairing Process
Hi all,
- What Keys Are Generated During The Bluetooth Pairing Process Manual
- What Keys Are Generated During The Bluetooth Pairing Process Computer
What Keys Are Generated During The Bluetooth Pairing Process Manual
Jan 19, 2014 As far as Bluetooth LE is concerned, pairing and bonding are two very distinct things. The short explanations are that pairing is the exchange of security features each device has, and creating temporary encryption. Bonding is the exchange of long term keys AFTER PAIRING HAS OCCURRED, and STORING THOSE KEYS FOR LATER USE. Jun 03, 2005 Sniffing the airwaves. During pairing, two Bluetooth devices establish the 128-bit secret “link key” that they then store and use to encrypt all further communication.
Just a quick writeup on the difference between pairing and bonding, since these terms get used interchangeably. I think this has to do with the usage of ‘pairing’ in Bluetooth Classic, or BR/EDR.
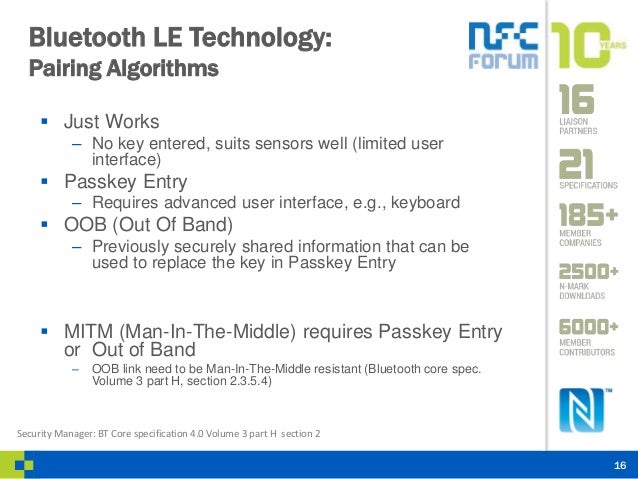
As far as Bluetooth LE is concerned, pairing and bonding are two very distinct things. The short explanations are that pairing is the exchange of security features each device has, and creating temporary encryption. Bonding is the exchange of long term keys AFTER PAIRING HAS OCCURRED, and STORING THOSE KEYS FOR LATER USE. Pairing is not the creation of permanent security between devices, that is called bonding. Pairing is the mechanism that allows bonding to occur.
What Keys Are Generated During The Bluetooth Pairing Process Computer
Pairing
Pairing is the exchange of security features. This includes things like i/o capabilities, requirement for man-in-the-middle protection, etc. The client side begins this exchange. The client essentially says ‘hey, i’d like it if you had these features’. The server replies, ‘yeah, well, this is what I can do’. Once this exchange is made, the security that will be used has been determed. For example, if a server supports just noInput/noOutput for i/o capabilities, the Just Works pairing mechanism is going to be used.
Once the pairing feature exchange is complete, a temporary security key is exchanged and the connection is encrypted, but only using the temporary key. In this encrypted connection, long term keys are exchanged. These keys are things like the (long term) encryption key to encrypt a connection, and also things like a digital signature key. The exact keys exchanged are determined by the security features of each device.
Bonding
Axure RP 8 License Key Generator & Crack Full Version Download. Axure RP 8 Crack with License Key Full version is an advanced yet easy-to-use powerful tool for website wireframing, prototyping and specification tools required to visualize an innovative web design. With this software Axure RP 8 License Key you can create beautiful wireframes with text, boxes, shapes, placeholders, and more. Axure RP Pro 8 Crack + License Key Generator Windows + MAC Axure RP Pro 8 Crack enables you to produce prototypes of websites and apps without coding. You can create simple click-through mockups or extremely functional, rich prototypes with conditional logic, dynamic content, animations, drag and drop, and calculations. Axure rp 8 license key.
This really just means that after the pairing features exchange and the connection has been encrypted (these two together are called ‘pairing’), and keys have been exchanged, the devices STORE and USE those keys the next time they connect. Keys can be exchanged using the bonding procedure, but that does not mean they are bonded if the keys are not stored and used the next time.
With IDM 6.25 Serial key incl, you can download a similar document in the meantime at triple or more circumstances expanded speeds just in the correct way. You should simply just introduce the idm 6.25 most recent at your pc and let it handle all your downloads fatigues. IDM 6.25 Key. Idm key generator 6.25.
If a device is bonded with another device, like a heart rate monitor and a smartphone, they can encrypt the connection without exchanging any sensitive security information. When the smartphone connects to the heart rate monitor, it can just issue a ‘turn on encryption’ request, and both sides will use the keys already stored, so nobody snooping can see a key exchange and therefore decode the messages being sent, as is done when pairing.
Hope that clarifies!